Dissecting a Spam Email - updated 2025
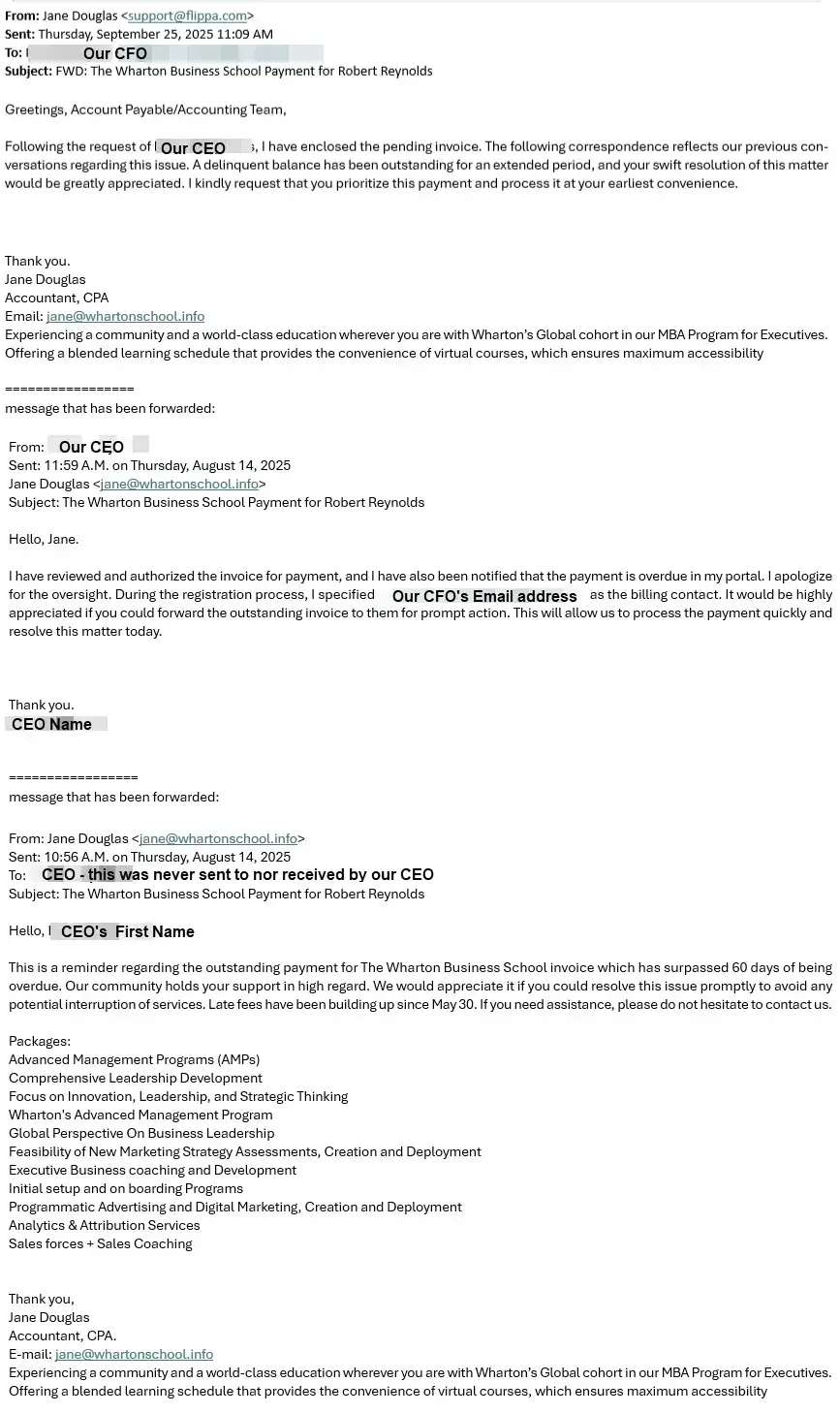
Our CFO recently received a very realistic email from a company indicating some training our CEO requested that was past due with a "note from the CEO to pay immediately." Without checking directly with our CEO by phone, this invoice could easily have been paid with no recourse for us to retrieve the payment.
Why It Matters More Than Ever
Attackers aren’t sending clumsy, typo-filled scams anymore. Today’s phishing emails and “callback” scams are polished, fast, and designed to steal logins or trick you on the phone—no malware required. One rushed click or reply can be enough to hand over an account.
The takeaway: learning to quickly dissect suspicious emails is now basic business hygiene.
What changed this year:
The new anatomy of a suspicious email (30-second scan)
Before you click, reply, pay, or share codes, run this quick check:
1
Sender reality check
Hover/tap to see the real From address. If it claims to be a coworker or vendor, verify using a separate channel (phone/Teams/Slack) — not by replying to the email.
2
Links & buttons
Hover to preview the URL. Real links match the brand’s domain. Beware look-alikes and link shorteners. Skip unexpected QR codes.
3
Urgency or unusual ask
“Act in 15 minutes,” “send the MFA code,” “call this number to unlock your account.” That immediate action pressure is often the entry point.
4
Attachments
Unexpected invoices/zips/docs — even in a real thread — are a red flag. Confirm using a different vehicle: phone, txt, Slack, etc.
5
Tone & context
AI means perfect grammar, so ask: Should this person be asking me this? If the request is money, credentials, gift cards, or MFA codes, treat it as hostile until proven safe.
Grab the printable version:
Copy of the email our CFO received. Click to enlarge.
If you already clicked or replied, do this now
What this means for small businesses
Remember Cyber Security is everyone's responsibility. Train your employees for Six-S. One-minute checklist (repeatable habit)
STOP
Take a breath before you act.
Source
Verify the sender through another channel.
Scan
Hover links, ignore QR codes, watch for look-alikes.
Story
Pressure + unusual ask = likely scam.
Safe Path
Visit the site yourself in a new browser tab or incognito mode.
Share
Report and delete.
